What we offer?
SaaS + Server maintenance
Keeping you secure, you’re free to focus on your business because we’ll take care of maintenance and system updates on an ongoing basis.
Configuration
Based on your needs, we prepare ready to plug & play systems whilst supporting you with our technical expertise.
A High Standard of Security and Compliance
- Private TKH Security Cloud for better control and heightened security.
- Data center in Amsterdam, NL/EU.
- Your dedicated SOC provided by TKH Security.
Hardware
Giving you full ownership of our hardware such as readers and locks, these come as one-time buy products.
Why?
Scalability
How can Access Control as a service transform your security scalability?
- Resource allocation, automatic updates, and centralized management seamlessly collaborate.
- Cloud platforms smoothly adjust to your organization’s growth or changing user numbers.

Cost Efficiency
Can ACaaS lead to cost savings?
- Upfront Savings: Set-ups no longer require a large investment in hardware such as expensive on-site servers.
- Shift to Operational Expenses: Businesses can embrace a flexible subscription model, paying only for what they use.

Real-time Updates
Can real-time updates be implemented across an organization?
- With ACaaS, modifying access privileges, updating authentication methods, or implementing new security measures reflect in real-time across the entire organization.

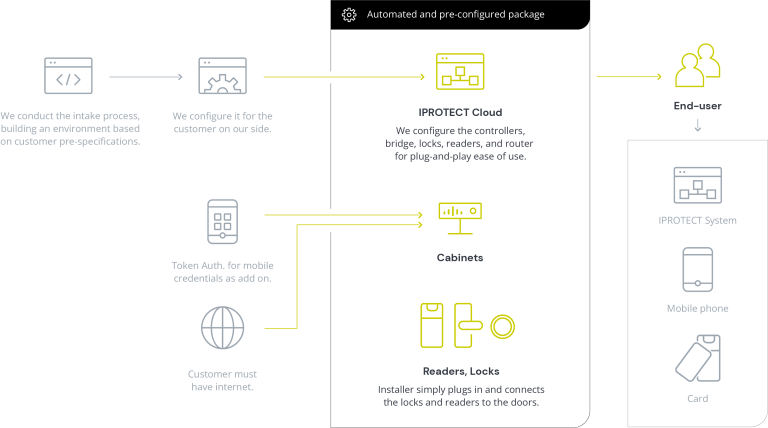
How it works?